Published: May 28, 2025 by Friedrich Vandenberghe
How can you protect your sensitive data and algorithms, even if they’re residing on untrusted devices? Encrypting the data on the disk is not sufficient. A hardware-based confidential computing environment, however, protects the data even in this case.
Normally, all data and algorithms on a device are accessible to someone who has root access to the device. This can be a competitor trying to steal your algorithms or an adversary trying to steal your user’s data. Even if it would’ve been encrypted on the disk, the adversary still has access to the decryption keys. However, placing this sensitive information in a confidential computing environment addresses these challenges.
In a confidential computing solution, the Trusted Execution Environment (TEE) or enclave isolates and protects data from software and individuals not explicitly authorized to access the TEE [0]. In the case of an attack by a malicious agent, the data is entirely inaccessible.
Confidential Computing on Arm Devices
Arm offers two kinds of confidential compute environments:
TrustZone works well for platform security use cases which are limited in scope. CCA is better suited to protect your VM or application [3]. Only TrustZone, though, is currently readily available [4].
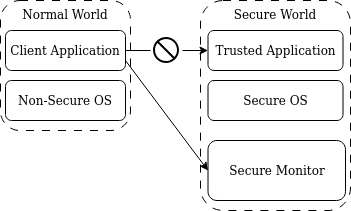
TrustZone divides the compute into a Secure world and a Normal world, respectively also called the TEE and the Rich Execution Environment (REE). Secure world software, called a Trusted Application (TA), has access to the Secure physical address space, which cannot be accessed by the Normal world. Typically, this address space is delineated at boot time. The division into two worlds is thus performed at the hardware-level. For software running in the Normal world to call a function in a TA, it needs to pass through a Secure Monitor.
An Analysis of TrustZone
The easiest way to use Arm TrustZone is to use an off-the-shelf TEE solution which follows the cross-platform GlobalPlatform (GP) specification [5]. Of the available TEEs, the open-source Open Portable Trusted Execution Environment (OP-TEE) [6] is the best candidate. This off-the-shelf solution for Arm TrustZone supports a plethora of platforms.
Applications executed inside the TEE solution are limited in their capabilities, e.g. only C is truly supported, C++ is supported up to GCC 11 [7] and Rust support is experimental [8]. This is mainly since if you would like to compile your application for OP-TEE, you have to use the libutils library [9] instead of libc [10]. This libutils library is rather limited in its capabilities. Additionally, OP-TEE also has no support for multithreading via libpthread [11].
Only C is truly supported, C++ is supported up to GCC 11 and Rust support is experimental.
Besides these restrictions, OP-TEE also dictates a certain program layout [12], e.g. the entry points in the main.c are predefined, which practically leads to a full rewrite when modifying an existing application to run inside TrustZone.
Performance-wise, running inside the TEE results in a 12 to 17 times overhead against the REE. This is a significant overhead, mostly caused by time-consuming memory operations [13].
TrustZone Use Cases
Organizations use confidential computing to unlock data silos, and meet global data privacy compliance requirements. In healthcare and pharmaceutical enterprises, the ability to engage in multiparty data collaboration safely and securely enables them to explore new treatments, develop new drugs, and improve patient outcomes more effectively than before. For financial services enterprises, confidential computing permits secure cross-industry collaboration to detect money laundering and other forms of financial crime.
All the following use cases provide examples of how Arm TrustZone can be leveraged to protect sensitive data and algorithms in organizations.
- HMAC-based One-Time Password
- Driver Protection
- Secure Storage
- Secure Over the Air Updates
- Samsung Knox
- Shield Neural Network Layers against Privacy Breaches
These applications are simple enough that the overhead brought upon by TrustZone is negligible, and that the necessary effort to compile them is doable.
HMAC-based One-Time Password
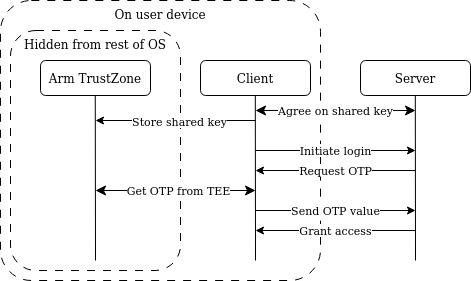
HMAC-based One-Time Passwords (HOTP) [14] are a popular choice for two-factor authentication. In this example [15] we have a client that wishes to get some resources on a server, for this they need to authenticate themselves. Here, Arm TrustZone is utilised to securely generate the OTP. When the user’s device is compromised, the adversary still has no access to the shared key. The Arm TrustZone TEE could also be leveraged as the validating service. Then, if the server is compromised, the shared key is still inaccessible.
First, the client and server need to agree on a shared key, which is stored in TrustZone. For this, there must be a secure channel between both parties–ideally between the TEE and the server, but OP-TEE currently only has support for TCP/UDP and not for TLS. Additionally, both need to start from a counter which is initialized to the same value.
To perform the actual client authentication, both client and server calculate the same HOTP and then the server validates that they’re the same. If this is the case, the server can then grant access to the resources which the client requested. Driver Protection
The firmware provided by vendors can include valuable IP which needs to be protected from reverse engineering, IP theft or malicious attacks [16]. Using TrustZone chip vendors can put their firmware in a protected, secure memory space, while still allowing users to interact with their device via their APIs.
Secure Storage
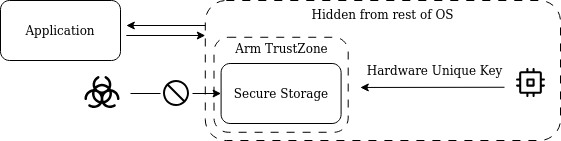
OP-TEE provides two secure storage implementations according to the GlobalPlatform TEE Internal Core API, this specification mandates confidentiality and data integrity [17].
Via the REE file system: This is the default Using the Replay Protected Memory Block (RPMB) partition of an eMMC device: A memory area that stores data in an authenticated and replay protected manner [18] It is possible to use both implementations simultaneously.
This secure storage in TrustZone can be utilised for a secure key store. First, TrustZone encrypts the keys via a hardware unique key burned into the chip. Afterwards, the encrypted key is stored in the secure storage. Keys would only be decrypted and used within the TEE and never accessible to the Normal World [19]. This way, confidentiality and data integrity is guaranteed.
Secure Over the Air Updates

To update the boot firmware, the system needs to get the authentic firmware image over a network. Furthermore, an attacker shouldn’t be able to roll the update back. For this, the OEM signs the image with its private key–the public key is provisioned by the downloading device. A non-volatile counter is incremented when the firmware is updated. This way, the signature is verified, and any rollbacks are detected [20].
Here, TrustZone ensures that the keys that are used to authenticate firmware images are protected and that firmware images cannot be rolled back.
Samsung Knox
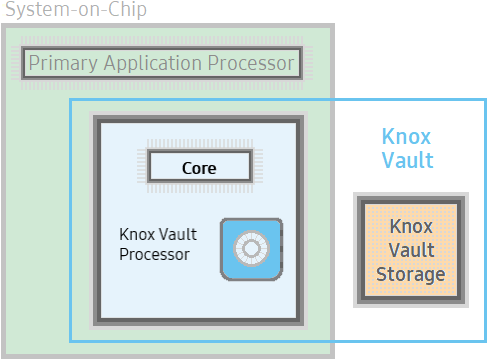
Samsung Knox is a proprietary security and management framework pre-installed on Samsung mobile devices. The framework consists of a multitude of system security mechanisms, heavily leveraging the security benefits of Arm TrustZone [21]. Inside this framework, there’s also Knox Vault [22], an extension upon the protection offered by TrustZone.
In Samsung Knox, the highly sensitive software runs inside the secure world. Thanks to Arm TrustZone components that are marked secure, e.g. a fingerprint reader, can only be accessed inside the secure world.
Knox Vault is available on select devices and extends upon this by providing an independent, tamper-proof, secure subsystem with its own processor, memory, and an interface to dedicated non-volatile storage–wherein it stores the sensitive data such as cryptographic keys and authentication data. Even if the main application processor that runs Android is compromised, the Knox Vault protects secrets and guards against hardware attacks such as probing and fault injection.
Shield Neural Network Layers against Privacy Breaches
TrustZone shields critical deep neural-network layers against privacy breaches like membership inference attacks. In a membership inference attack, the attacker manipulates the model’s training data to cause it to behave in a way that exposes sensitive information [23].
DarkneTZ [24] is an application that illustrates how OP-TEE can be leveraged to shield critical neural-network layers. It ports selective components of Darknet [25], a deep neural network framework, for secure world execution. Notably, to thwart inference attacks, it delegates deep layers to the secure world while the rest layers are operated in the normal world. Typically, the last layers are delegated, as these have a higher probability of leaking private information about training data.
Conclusion
Using a confidential compute solution is paramount to protect sensitive data and algorithms on untrusted devices. For Arm platforms, the only readily available solution is Arm TrustZone. TrustZone comes with hefty restrictions: the required code changes and the significant overhead. Therefore, it is best to keep the footprint of the secure application to a minimum.
Nevertheless, Arm TrustZone does have its use-cases:
- HMAC-based One-Time Password
- Driver Protection
- Secure Storage
- Secure Over the Air Updates
- Samsung Knox
- Shield Neural Network Layers against Privacy Breaches
When Arm CCA becomes widely usable, the required code changes and the significant overhead should no longer be present.